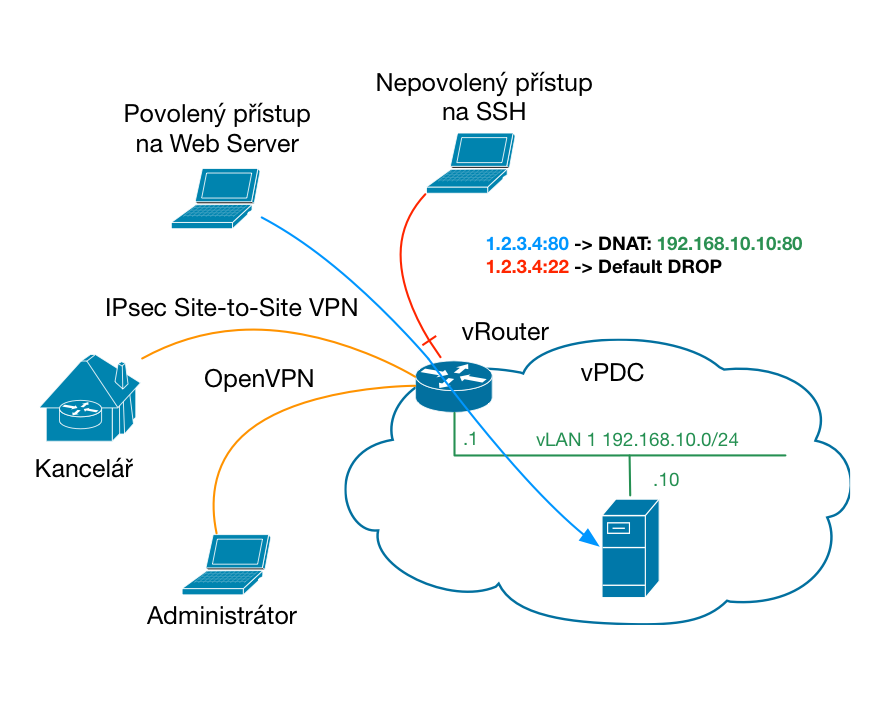
- Analýza bezpečnosti v podnikovém cloudu
- Adastra - datový sklad pro IKEA
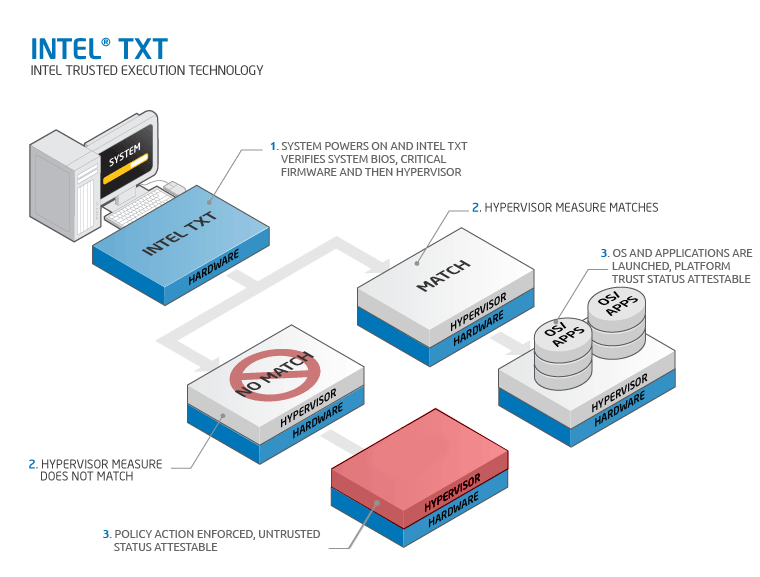
- Intel® Trusted Execution Technology (Intel® TXT) - content
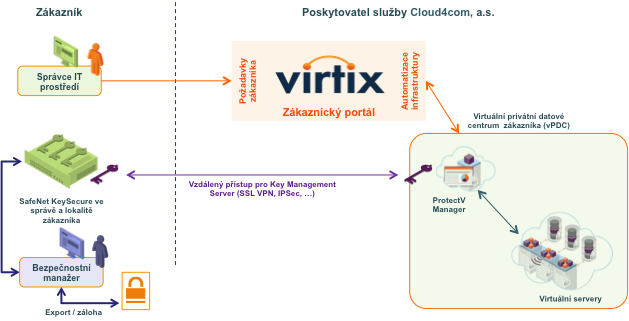
- Cloud4com - Customer Testimonials
- Virtix – Videos on Cloud4com YouTube Channel
- Gemalto Case Study
- Intel Case Study
- Intel Case Study 2
- Activating Intel® TXT
- Trusted Compute Pools with Intel® TXT
- One-Stop Intel TXT Activation Guide
- Dupont Private Cloud Study
- Intel Trusted Execution Technology
- Intel Case Study UOL